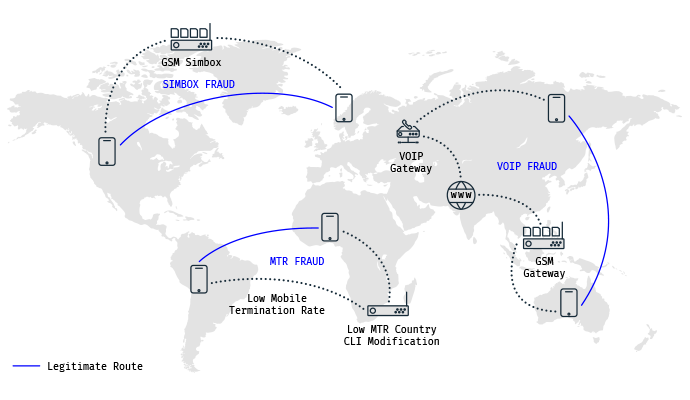
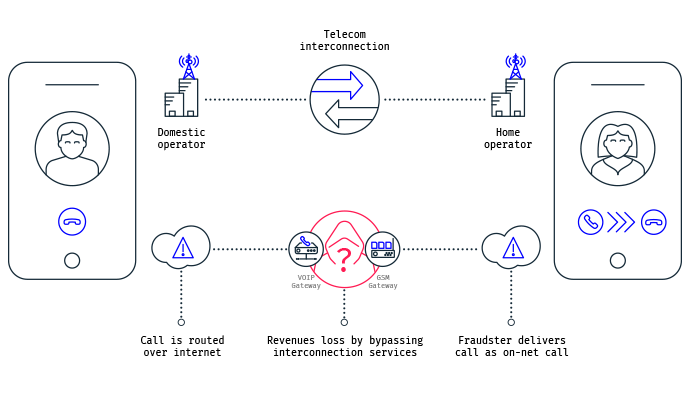
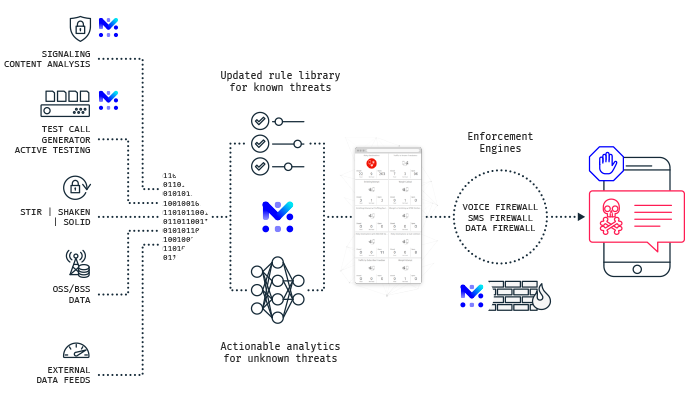
Roaming and Core Network
Risk Management
-
Revenue Assurance
- Usage Assurance
- Provisioning Assurance
- Rating & Billing Validation
- Prepaid Balance Validation
-
Fraud Management
- Revenue Share Fraud
- Bypass Fraud
- Roaming Fraud
- CLI Spoofing & Robocalling
- VoIP & SIP Fraud
- Dealers Fraud
- Subscription Fraud
- Data Fraud
- Telecom Wholesale Fraud
- SMS Bypass Fraud
-
Business Assurance
- IoT Assurance
- Collections Assurance
- Mobile Money
- Partner Incentives Assurance
- Cost and Margin Assurance
- Flash Calls
-
Business Operations
- Collections Management
-
Proactive Risk Management
- Proactive Revenue Assurance
- Proactive Fraud Management
- Proactive Business Assurance
Network Security
-
Signaling Firewall
- Cross Protocol Firewall
- SS7 Firewall
- Diameter Firewall
- GTP Firewall
- SIP Firewall
- Signaling Outbound Firewall
- Security Edge Protection Proxy (SEPP)
-
SMS Firewall
- A2P Grey Route Firewall
- SMS SPAM Firewall
-
Security Services
- Threat Intelligence
- Penetration Testing Services
-
Cyber Surveillance
- Threat Monitoring
Testing and Monitoring
-
Domestic Network Testing
- SITE Platform
- 5G SA & NSA Performance Testing
- Core Network Testing
- Automation Framework
- RoboShark Automated PCAP Analysis
- Smartphone-based Testing
- Emergency Services Testing
- Video Performance Testing
- IoT & eSIM Performance Testing
- IMS and VoLTE Testing
- CS Voice, Data & Messaging Testing
- Mobile Money Testing
-
International Network Testing
- Roaming Quality Testing
- Global IoT Connectivity Testing
- Performance Intelligence
- VoLTE Roaming Testing
-
Lab & Performance Testing
- dsTest Platform
- 5G Lab Testing
- 4G Core & VoLTE Testing
- Cellular IoT Testing
- 3G 4G 5G Functional & Compliance Testing
- Automated Signaling Firewall Testing
- dsTest Support Materials
Internet of Things (IoT)
Service & Network Assurance
Check our Services
Check out our exclusive insightful content